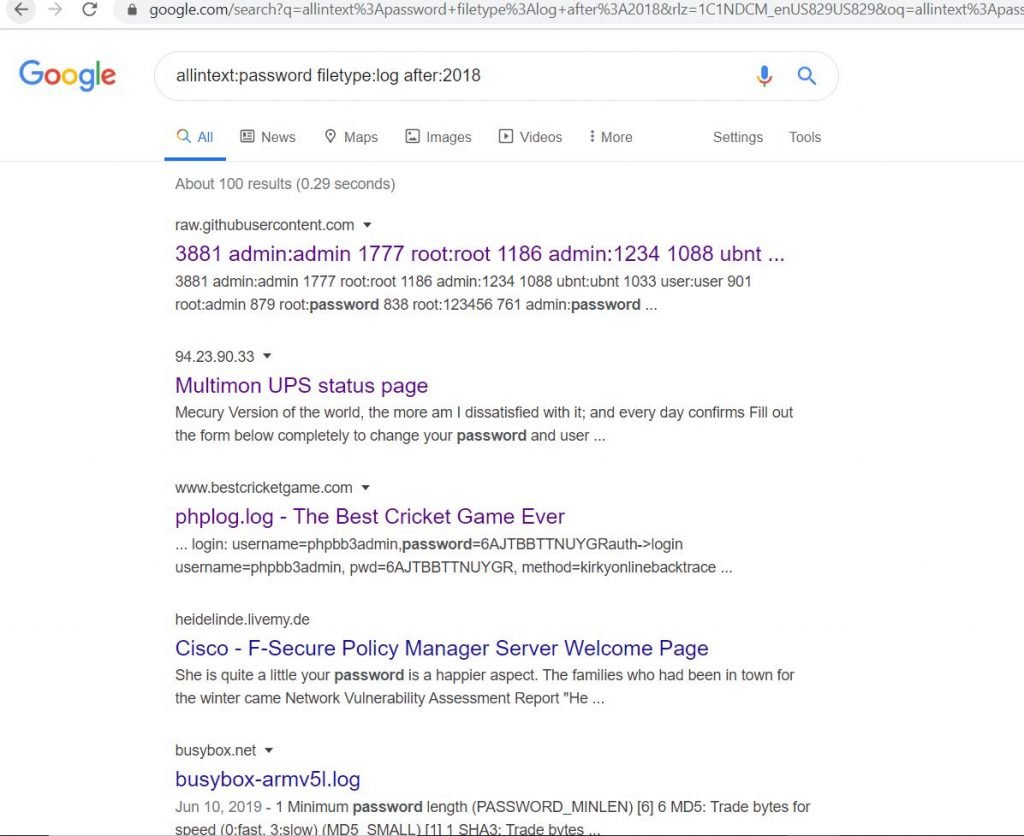
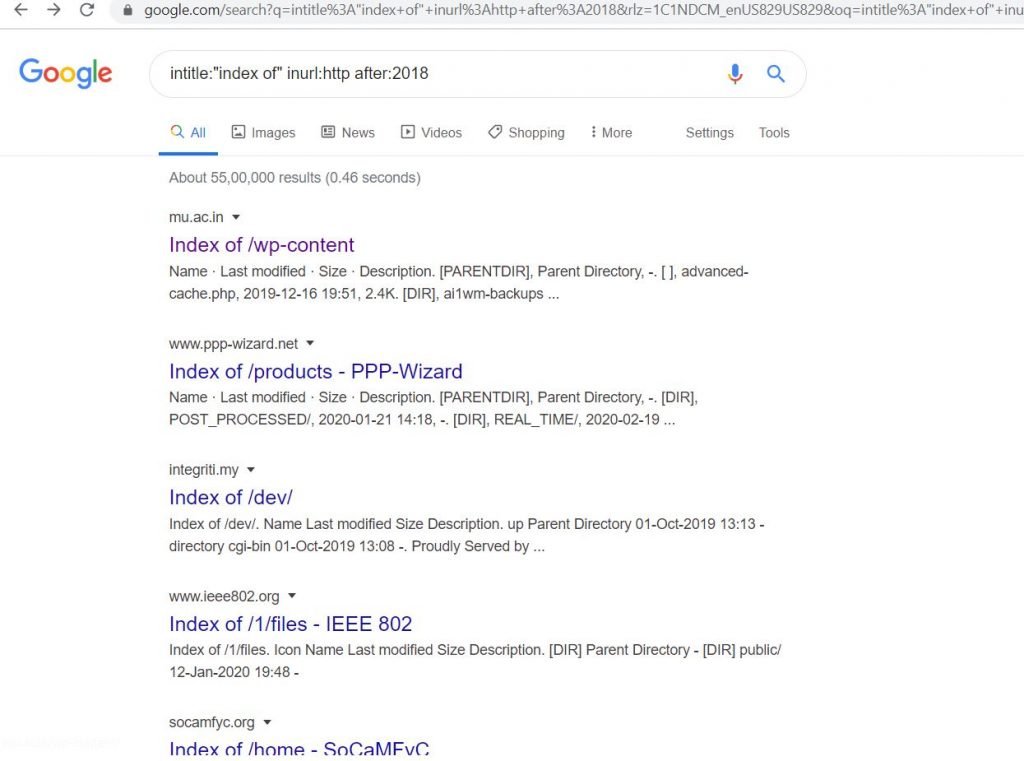
TR Bug Hunters on Twitter: "🛡️ Find Passwords, Exposed Log Files with Google Dorks 🛡️ #bugbountytips #bugbountytip #bugbounty #cybersecurity #infosec #ethicalhacking #hacked #hacking https://t.co/Hi16andKhH" / Twitter

Jinwook Kim on Twitter: "Google Dork operator - Live cameras - inurl:top.htm inurl:currenttime (intitle:"webcamXP 5")(inurl:"lvappl.htm") https://t.co/kvbn2B8hAu" / Twitter
![Differentiated historical demography and ecological niche forming present distribution and genetic structure in coexisting two salamanders (Amphibia, Urodela, Hynobiidae) in a small island, Japan [PeerJ] Differentiated historical demography and ecological niche forming present distribution and genetic structure in coexisting two salamanders (Amphibia, Urodela, Hynobiidae) in a small island, Japan [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/13202/1/fig-3-full.png)
Differentiated historical demography and ecological niche forming present distribution and genetic structure in coexisting two salamanders (Amphibia, Urodela, Hynobiidae) in a small island, Japan [PeerJ]

A Hacker's Guide to Google Dorks. Want to get more out of your Google… | by CoolTechZone - Cyber Security Labs & News | Medium
![Differentiated historical demography and ecological niche forming present distribution and genetic structure in coexisting two salamanders (Amphibia, Urodela, Hynobiidae) in a small island, Japan [PeerJ] Differentiated historical demography and ecological niche forming present distribution and genetic structure in coexisting two salamanders (Amphibia, Urodela, Hynobiidae) in a small island, Japan [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/13202/1/fig-2-full.png)
Differentiated historical demography and ecological niche forming present distribution and genetic structure in coexisting two salamanders (Amphibia, Urodela, Hynobiidae) in a small island, Japan [PeerJ]

Google Dork: hacking di siti web grazie alla ricerca su Google | Marino Luigi: Senior iOS Developer, IT Project Manager e CTO